

PC gaming is open source, allowing players to modify code and system files while playing or before playing the game. A result of any game that runs multiplayer typically uses some anti-cheat system: BattlEye, Valve Anti-Cheat, or TruePlay to minimize hackers. This is less often for console gamers, as the system is closed source and cannot run code along with the game simultaneously.
While hackers have become less relevant, more so in modern games, as anti-cheats are becoming more sophisticated. One bypass is putting cheats and hacks into the game before booting it and activating the anti-cheat program. Riot Games is taking a new route with anti-cheat systems. Valorant uses a program called Vanguard. Vanguard is quite different from most anti-cheats as it is a vgk.sys or a kernel-level driver.
Most operating systems have levels of access privileges often called and portrayed as protection rings. Ring zero or kernel level access in Windows allows the driver to run a system administrator, or with maximum privileges. The reason that a computer needs to reboot after installing Valorant is to have Vanguard running at the administrator level privileges.
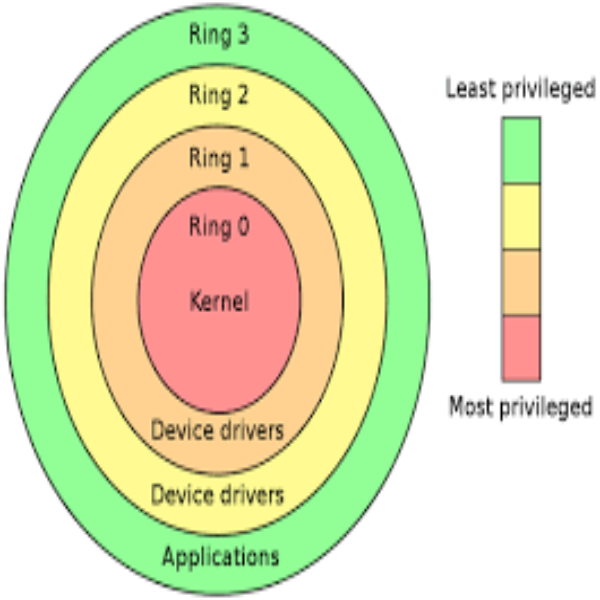

A driver that runs in ring zero or with kernel-level access is commonly called a “root-kit” and is most commonly seen with types of malware designed to hijack a computer. As of right now Vanguard immediately starts running upon booting the computer and Valorant will not play without Vanguard running giving the game an all clear. This is designed to stop cheaters from loading hacks before starting the game, but this can be bypassed through system management mode. Something cheaters have already done in Valorant.
Riot developer going by the Reddit name RiotArkem has responded to the concern that was aired, “We’ve tried to be very careful with the security of the driver. We’ve had multiple external security research teams review it for flaws (we don’t want to accidentally decrease the security of the computer like other anti-cheat drivers have done in the past). We’re also following a least-privilege approach to the driver where the driver component does as little as possible preferring to let the non-driver component do the majority of work (also the non-driver component doesn’t run unless the game is running),” Riot developer going by the Reddit name RiotArkem has responded to concern that was aired. RiotArkem did not disclose which third parties tested Vanguard for vulnerabilities.
The Vanguard driver does not collect or send any information about your computer back to us.
RiotArkem assured players that Vanguard can be manually uninstalled and reinstalled at will, but Valorant will not run without it. As well, Valorant cannot be played inside a virtual machine. This is most likely another protection as most hackers virtualize the games that they are exploiting, but this means that Riot will have access to the main operating system of the computer along with its information.
It’s important to note that Riot is owned by Tencent. The largest of China’s video game companies. As with all Chinese corporations, a member of the Communist Party of China sits on the board of directors, who in Tencent’s case is the founder and CEO of Tencent, Ma Huateng. Ma Huateng currently serves on the 13th National Peoples Congress as a deputy. It is not likely that Tencent or the Communist Party of China would collect data on gamers, but Vanguard is still a backdoor into a computer that will inevitably be exploited by somebody.
It is unknown if Vanguard will be coming to Riot Games’s other titles such as League of Legends.
Play games, take surveys and take advantage of special offers to help support mxdwn.
Every dollar helps keep the content you love coming every single day.
